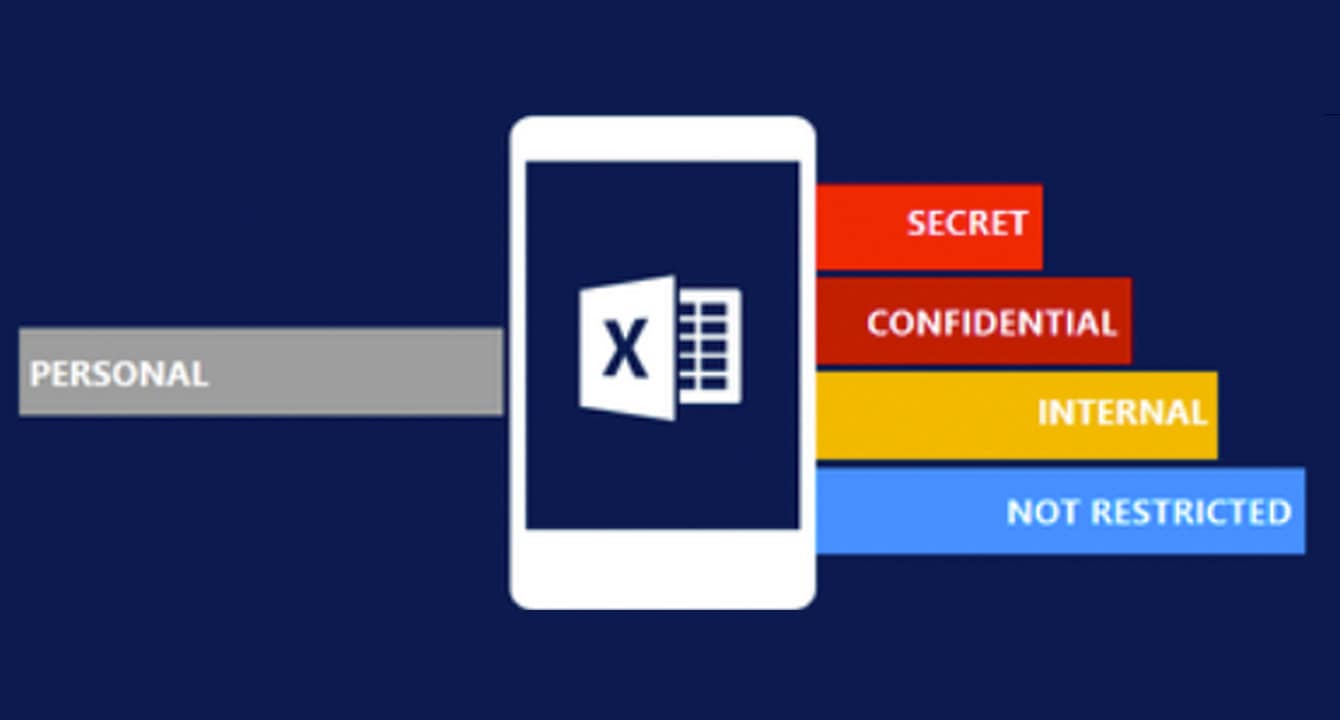
Data Leakage Prevention Solutions
DLP (Data Leakage Prevention) is a technology to prevent valuable data in the information security be found by others. Today, the companies have to determine and monitor all data they use or keep and to provide security. It is important that there are DLP solutions in your company or for you to be prepared for official audits.
This system which prevents important data of the companies be found by others can be mostly implemented in all network structure or put a barrier at the final user level.
Data Governance
Data Governance is the general management of data availability, conformity, usefulness, integrity and security in a company. It is possible to determine by who and how sensitive data is accessed, to implement access rules, to provide access to folders and files only the employee is authorized to with these solutions. The functions of data governance solutions are determining access habits of the users and detecting abnormal access, categorizing data based on folders and reducing risks by assigning data responsible.
Firewall Solutions
We offer firewall solutions to eliminate increasing risks at the present time, to take necessary precautions and to provide safe function of your company thanks to business partnerships with the leading trademarks in the sector.
The firewalls which are categorized as traditional (UTM) and Next Generation check basically your incoming and outgoing network traffic and prevent people who are unauthorized or you do not want from accessing your computer or your computer network by using various ways. In next generation firewalls, the rules based on user or group can be typed instead of IP and some permissions based on application can be given. Besides basic firewall functions, some features such as IPSEC, VPN, IPS, URL filtering, anti-virus, hotspot etc. can be offered with next generation firewalls.
DOS/DDOS Protection
Distributed denial of service (DDoS) attack is one of the most important cyber threats of our present day for companies. All of the events which aim to prevent any presentation, broadcasting or trade are conducted to prevent the actual job by creating actual or modified density are in the scope of DDoS. These attacks are conducted by basically consuming bandwidth or using a vulnerability on the service. The hardest part of preventing DDoS attacks is separating of actual user traffic and attack traffic under dense request. For separation and proactive protection, hardware based DDoS protection solutions are necessary.
Malicious Code Analysis and Threat Management Solutions
These solutions which enable you to make malicious code analysis and threat management are named as APT (Advanced Persistent Threats). Malicious contents, exploits, trojans, callback traffics, backdoor attempts, cryptolocker and ransomware variants can be detected with APT solutions. Malicious software which are just discovered and known as zero day, not based on signature is detected and prevented by operating in different operating system images in these solutions.
Constant Security Verification and Improvement
Constant security verification and improvement software helps you to measure cyber threat preparation for 24/7 and to apply rapid improvement. These solutions provide very important added values such as following current threats, to measure your security maturity level, to increase the efficiency of your security solutions and to manage security risks. By using this software, we can help your evaluation, measurement and improving procedures in security processes and measure your cyber security infrastructure and make it effective and strong.
Server Security
There are virtual patch management in the servers, protection against malicious software for web, firewall based on main machine, unauthorized access detection/prevention, integrity monitoring, record inspection, encryption and solutions providing comprehensive security features and containing reliable SSL certificates. You can manage your server security from a single center by the help of agents installed by using these solutions.
Mobile Device Management
They are the solutions which check the conformity of corporate mobile devices or personal mobile devices used with the model of bring your own device (BYOD) according to the corporate policies and allow you to manage your devices and applications on them from a single center. It is important to create a safe working environment on mobile devices so that there is no security risk in case the mobile devices are lost or stolen. Since the security solutions of mobile devices have features such as remote wipe security management and control and safe e-mail service, these solutions have gained importance.
Web Application Firewalls
They are solutions developed to protect web applications from web-based attacks. It is necessary for you to analyze your incoming and outgoing web traffic deeply and take precautions. WAF solutions allow to detect and prevent critical level attacks such as OS Command, XSS, SQL Injection.
Vulnerability Scan
Vulnerability scan solutions allow you to scan operating systems and applications and to report vulnerabilities. It is important to detect and report vulnerabilities in order to close gaps in your system and to prevent potential access attempts. You can use these solutions to control vulnerability analysis for network and system infrastructure in certain intervals and to take action.
Privileged User Management and Inspection
The management of authorized (privileged) accounts is one of the most important issues in management of security processes. In most of the targeted attacks, the aim is to get a privileged account information and to use these authorities. It is important to manage, store and record accesses to these accounts and the passwords of the critical accounts in terms of both security management and compliance to the regulations. These solutions allow you to keep your all accounts and passwords safe with the digital case approach. In addition, they provide information by whom, when and how the privileged user accounts are used.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a technology which increase security level by providing an extra protection layer in addition to your user name and password. It is possible to use multi-factor authentication mechanisms when accessing a computer, application or a network. The attacks made through social engineering and phishing to obtain user information are prevented with these solutions.
PDPL Consultancy
There are many important changes for the companies with the Personal Data Protection Law of 6698. Some rules and obligations are determined in issues of storing, processing and providing security of the personal data for all organizations and institutions by the law. If the conditions of the law are not fulfilled, the real and legal persons may face imprisonment besides penalties. Even though some obligations are determined by PDPL, data recording and data transfer are not forbidden if they are carried out in accordance with the law.
Since the transition period has ended, it is important to provide compliance processes to PDPL rapidly and efficiently. For this reason, taking consultancy service from competent persons who are specialized in this subject provides advantage in terms of effort and costs. Since there are administrative, legal and technical processes in compliance to the law, a consultancy service covering all fields facilitates your processes.
As Provis, we offer end-to-end consultancy services in PDPL Adaptation Projects with K&P Legal Law Firm which is our business partner. We help our customers in taking all administrative, legal and technical precautions specified in the law for our customers with this service.
DLP Project Consultancy
If Data Leakage Prevention (DLP) Projects are not properly configured and managed, it is hard to achieve target. There are processes which will require inclusion of all teams with IT team in DLP projects. It is not possible to put DLP projects into practice successfully and efficiently without completing the steps of taking approval of the management, determining and categorizing sensitive and critical data, detection of the movement of the data on the move, determining of safe data flow paths and creating of data map. DLP policies are specially prepared for the customers in accordance with the data map created.
We complete projects by offering consultancy services besides product positioning in DLP and data categorization projects. In this context, we support our customers from the beginning up to completion of the project process.
Penetration Test Service
A penetration test is performed for a certain purpose and/or a scenario unlike vulnerability analysis.
It is one of the first steps of proactive security to test, check and report all kinds of vulnerability of the information systems by an external company and/or an institution. External tests are performed to disclose vulnerabilities by approaching all kinds of security gaps that the companies do not realize from a different aspect and working in a coordinated way. We offer these works as black box and white box as inner and outer tests for our customers. It is required to fill the scope form and to determine the details of the work to be done before working on it.